Information Security
▪ ChipMOS Information Security Policy
Established Information Security Dedicated Unit
In 2014, ChipMOS set up an "Information Security Management Committee" with the general manager as the chairman and the first-level managers of each business unit as the main members. The committee is responsible for formulating information security policies, supervising the implementation of information security plans, and managing and reviewing information security-related matters and coordinating communications to ensure the effectiveness of the implementation of the information security management system and enhance the information security of the company's operations. An annual management review meeting is held annually, and the results of cybersecurity governance oversight are reported to the board of directors annually.
The Information Security Office (hereinafter referred to as the Information Security Office) was established in 2022 and is affiliated to the Information Security Committee. It designated personnel to engage in information security-related tasks and take the responsibility for information security affairs. There is one information security supervisor and two information security personnel. They are responsible for planning the company's information security system and information security protection network defense, and take proactive prevention and control measures to minimize the impact of information security incidents, ensure the maintenance of organizational operations and quickly resume business activities.
[Risk Management] Facility and Physical Management
ChipMOS continues to strengthen its backup systems, software and hardware capability upgrades, IT system business continuity plans (BCPs), etc., and have completed ISO 27001:2022 international standard certification in 2024 to enhance the organization's information security resilience and maintain continuous business operations.

1. Strengthen the data backup and restoration mechanism
Strengthen data backup space and data synchronization to restore operational data as quick as possible, e.g., system upgrade, including the database (DB) and non-database (OA) of all fabs.
2. Information security health diagnosis
From local inspection to comprehensive identification of factory security risks and vulnerabilities, use external security tools to review the current security system architecture and defense level.
3. 3C control measures
To effectively protect the Company's information security management, employees shall comply with the 3C management mechanism and use mobile media according to the control measures.
4. Identity authentication mechanism
To ensure the security of remote login, an identity authentication mechanism (2FA, two-factor authentication) is established to enhance data security.
5. Compliance with Information Security Laws and Regulations
(1) As for regular review:in 2024, there were the amendments to seven laws and regulations of the Criminal Code, Personal Data Protection Act, Copyright Act, Trade Secrets Act, Enforcement Rules of the Personal Data Protection Act, Taiwan Stock Exchange Corporation Procedures for Verification and Disclosure of Material Information of Companies with Listed Securities, and Information and Communication Security Control Guidelines for TWSE/TPEx-Listed Companies.
(2) The "Information of Companies with Listed Securities, and Information and Communication Security Control Guidelines for TWSE/TPEx-Listed Companies" has been included for implementation. The third-party certification will has been conducted in November 2025 to maintain the validity of the certificate.
6. Simulation of information and communication security crisis and disaster recovery drills
A total of 43 sessions were held in 2024, with a completion rate of 100% to improve the ability of IT personnel to take immediate response measures in the event of an information security incident and prevent information security hazards.
7. ISO 27001 certification
2022 version of the international standard for upgrading of information security resilience, professional consultants are hired for guidance, and internal ISMS regulations are revised to comply with the requirements under the new version of ISO 27001: 2022. The certificate successfully obtained the certification in November 2024.
Information Security Training for Employees
According to the 2023 CIO Insight, Virus and SPAM(60.9%) and Social Engineering Scams (29.5%) were the most serious security threats. In view of this, information security education and training in four major areas were planned in 2024.
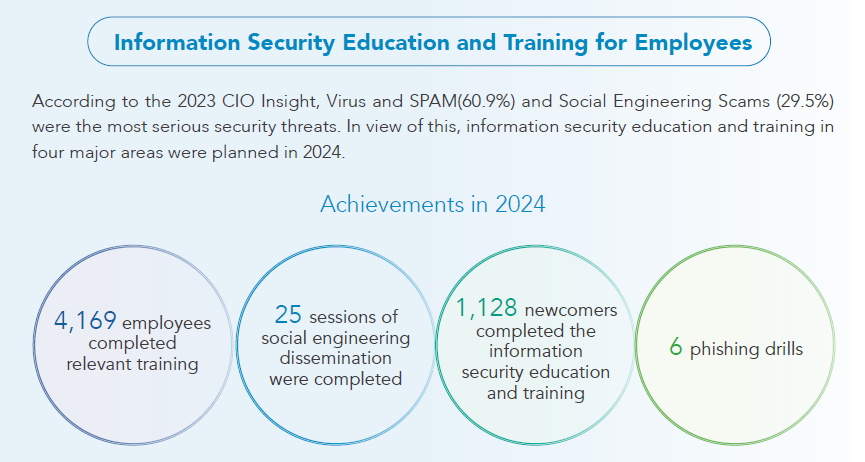
◆ Annual information security training for newcomers
Frequency: As per the employee check-in schedule
Content: Describe the information security policy, the Company's information security regulations, information security rewards and punishments, and 3C control measures.
◆ Social engineering dissemination
Frequency: no fewer than once per month
Content: Promote common social engineering attack techniques to raise awareness among colleagues and prevent falling victim to such attacks.
◆ Information security training for employees
Frequency: annually
Content: Audit illegal software usage, promote preventive measures against ransomware incidents, raise awareness on phishing scam emails, and establish regulations for USB drive usage control.
◆ Phishing drill
Frequency: once every two months
Content: Simulate sending targeted emails with specific subjects, including links or attachments, to measure click rates and test employees' awareness of information security.
[Preventive Management] Information Assets Management
ChipMOS establishes an inventory of information assets based on the value of information assets (confidentiality, integrity and availability) and the criticality to organizational operations, and manages them by category. It also establishes standards for information asset risk assessment to identify information security risks caused by information asset weaknesses and threats, and takes countermeasures or control measures based on the risk assessment results to reduce the risk of information assets being damaged.
We execute risk assessment of annual information assets and information security every year, and prepare the "Information Security Asset Risk Assessment Table" based on the value of the information assets, threats, vulnerabilities, and impact". In addition to the "Risk Improvement Plan", we formulate and implement the risk response measures for high-risk information assets to reduce their risk and avoid affecting the continuous operation of the information system.。
Information Asset Management:
1. Newly acquired hardware assets are tested and accepted by the applicant
2. An information asset inventory system and information asset risk assessment are established
3. The changed/new hardware information assets are tested before going live to ensure that the functions meet the requirements and are compatible with the existing system.
4. When important information assets are changed, their availability and performance shall be considered, and the performance of various resources shall be confirmed to meet the current operational needs. Future Operational performance requirements shall also be estimated. Capacity management may include hard disk capacity, CPU performance, network bandwidth, etc.
[Preventive Management] Information Security Incident Reporting and Accident Management
As a member of the Taiwan Computer Emergency Response Team / Coordination Center (TWCERT/CC) to assist companies in providing consultation and coordination services when information security anomalies are discovered, and address and correct them in a timely and appropriate manner. These measures can prevent the occurrence of abnormal information security problems and thereby improve the level of information security. In addition, to ensure that information security incidents are promptly reported according to the procedure, and necessary contingency measures are taken and an incident learning mechanism is established to minimize the resultant damage, we conduct incident and accident management, cause analysis, corrective process, and preventive measures in accordance with the information security incident management procedure.